Sample Exams of Cybersecurity
In these series we have some “Sample Exams of Cybersecurity”, “Practice Cybersecurity Examinations”, “Cybersecurity Test Previews” and “Mock Cybersecurity Tests”
What organizations need to invest in improved security practices?
- investing in cybersecurity training for all staff so that they are aware of and able to spot a cyber attack
- enforcing two factor authentication for employees accessing files and applications that contain sensitive data
- maintaining log files and ongoing monitoring to identify anomalous behavior that might indicate a data breach
- storing the passwords of customers using a combination of salting and robust hashing algorithms
- separating cloud-based resources from the public Internet into an isolated private network segment
- granting employees access to personal data and internal systems only via a secure VPN connection.
Data Breach:
- What was taken? Personal information, financial data, or sensitive company data.
- Exploits: Typically involve phishing attacks, malware, or vulnerabilities in web applications.
- Prevention: Employ strong access controls, regular security training for employees, and keep software and systems up to date. Implement encryption and multi-factor authentication.
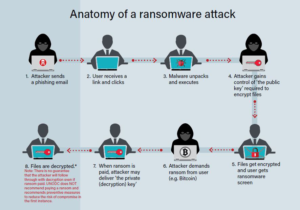
Ransomware Attack :
- What was taken? Access to and encryption of data until a ransom is paid.
- Exploits: Usually initiated through phishing emails or exploiting vulnerabilities in software.
- Prevention: Regularly backup data, use robust endpoint security software, and educate employees about the dangers of opening suspicious attachments or links.
Distributed Denial of Service (DDoS) Attack:
- What was taken? Temporarily disrupts a website or online service.
- Exploits: Overwhelms the target with a flood of traffic from multiple sources.
- Prevention: Implement DDoS mitigation tools, maintain redundancy in systems, and employ monitoring for unusual traffic patterns.
Insider Threat:
- What was taken? Sensitive information or malicious actions by employees or contractors.
- Exploits: Exploitation of internal access or data theft.
- Prevention: Implement strong access controls, monitoring, and auditing of user activity, and establish clear security policies and procedures.
Zero-Day Vulnerability Exploits:
- What was taken? Unauthorized access to systems or data.
- Exploits: Attackers target vulnerabilities in software that are unknown to the vendor.
- Prevention: Stay informed about software updates and patches, use intrusion detection systems, and employ good vulnerability management practices.
You can find other learning for Security by clicking here.